Ransomware: The PC Viruses You Must Fight Against! [Full Guide]
In today's digital age, it's inevitable to encounter malicious threats like malware and viruses. Malware is a type of software designed to harm your device, while ransomware is a specific type of malware that can encrypt your files and demand payment in exchange for the decryption key. These threats can cause significant damage to your PC, corrupting files and potentially rendering your computer unusable.

What Is Ransomware?
Ransomware is a type of malware that locks users out of their computers and demands a ransom payment in exchange for the decryption key. Once infected, users are unable to access their files until they pay the ransom, making it a highly destructive and potentially costly cyber threat.
The History of Ransomware
The first documented ransomware, the AIDS trojan, was introduced in 1989, but it failed miserably. However, over the years, more ransomware designs were created and tested, leading to various attacks through different schemes, marking a significant evolution in the history of ransomware.
In 2005-2006, Russia experienced a ransomware attack involving the TROJ_CRYZIP variant, which zipped and encrypted files, then demanded $300 in exchange for the decryption key, leaving behind a text file to inform users of the ransom.
In 2011, Trend Micro reported on a notable case of SMS ransomware, TROJ_RANSOM.QOWA, which displayed a ransomware page to users until they agreed to pay the ransom by dialing a premium number.
Russia was hit by a malicious ransomware threat that infected the Master Boot Record (MBR) of a system, preventing the operating system from loading. The malware copied the original MBR, overwrote it with malicious code, and forced the system to restart, displaying a notification to specific users.
The popularity and success of ransomware led to its spread to other European countries, with Trend Micro discovering infections that displayed a notification page instead of a ransom note.
A new wave of Ransomware infections was reported in Europe and North America, similar to the TROJ_RANSOM.BOV variant. The malware also spread to France and Japan after a French confectionery inadvertently served it, displaying a fake notice from the French police agency Gendarmerie Nationale.
How Does Ransomware Work?
Ransomware typically enters a system through spam emails, but other methods include downloading malicious software from the web, either directly or through fake ads called malvertising. Additionally, malware can spread through removable USB drives and chat messages.
Ransomware uses asymmetric encryption with a public-private key pair, where the attacker generates the keys and the private key is used to decrypt files stored on their server. The user must pay the ransom to access the private key and decrypt their files, with a deadline of 24-48 hours before the files are lost forever.
In addition to ransomware, viruses and malware are also commonly discussed threats. The article below explores the differences between these three types of malicious software, providing a clearer understanding of what sets them apart.
Virus, ransomware, and malware are often used interchangeably, but they have distinct meanings. A virus is a type of malware that replicates itself and can cause harm, but it doesn't need human interaction to spread. Ransomware is a type of malware that encrypts a user's files and demands a ransom in exchange for the decryption key. Malware, on the other hand, is a broad term that encompasses all types of malicious software, including viruses, ransomware, and other types of malicious code.
Virus vs. ransomware vs. malware, what is the difference? Which one is most harmful to our computer system and personal data?
Defend Against Ransomware?
We will discuss measures to avoid Ransomware risk and steps to remove it if it infiltrates your system.
Prevent Ransomware?
To prevent your system from getting attacked by Ransomware, it's essential to stay informed and take proactive measures. Always keep your operating system, software, and security updates up-to-date, as these patches often include fixes for vulnerabilities that Ransomware can exploit.
- Use security software and keep it up to date
Security software is essential to protect your system from unauthorized sources or viruses. Regularly updating this software ensures you have access to the latest features and improved protection, helping to safeguard your system from potential threats.
- Use only secured networks and sites
Cyber attackers can easily trace your internet activities through public Wi-Fi networks, so it's best to avoid them. Instead, install a VPN to ensure a secure internet connection wherever you go.
- Secure your data and files and backup them continuously
Backups won't prevent Ransomware, but storing them securely in the cloud or external hard drive can help prevent deletion. Use backup systems with no direct access to the backup files to prevent Ransomware from targeting them.
- Provide awareness through campaigns or other sources
Be cautious of unverified emails and files, and regularly monitor employees to prevent any issues.
- Stay informed
Keep yourself informed about the latest ransomware news and variants, and be prepared with decryption tools that some companies have introduced, in case your system gets attacked.
Remove Ransomware?
Paying the ransom doesn't guarantee that your files will be unencrypted, and it may encourage cybercriminals to continue their activities. Instead, focus on installing security software and backing up your important data to protect yourself from ransomware attacks.
Below we will discuss some steps to remove the Ransomware.
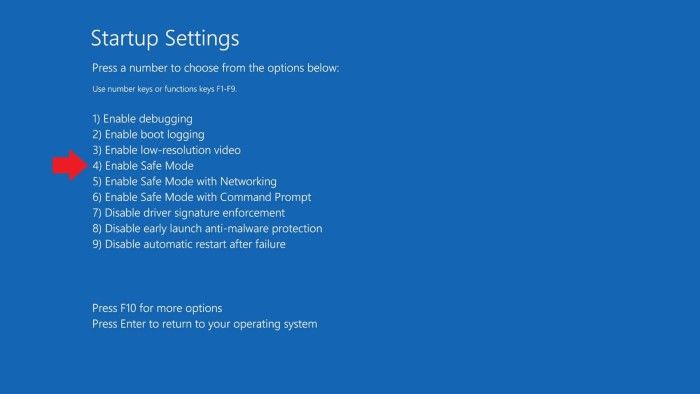
Step 1. If your system is slowing down, shut it down immediately and disconnect the internet connection. Booting in "Safe Mode" will prevent the malware from receiving commands from the control server, thereby slowing down your system.
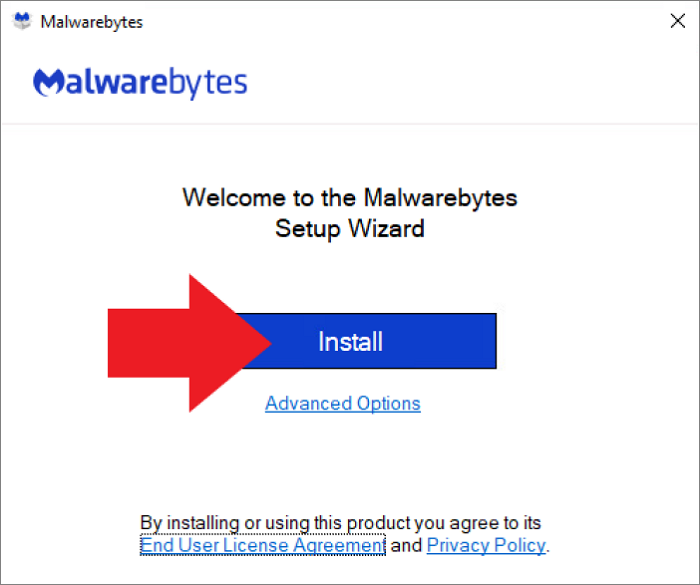
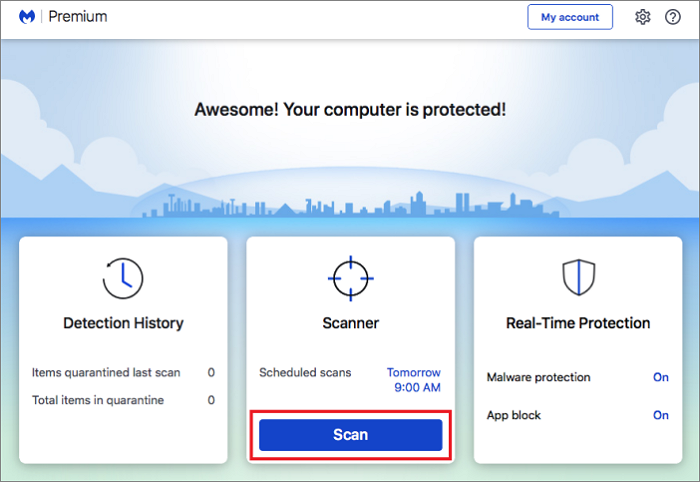
Step 2. Install anti-malware software and run a full system scan to remove the threat.
Step 3. Restore and restart your PC to a safe state.
- Notice:
- You can try using free decryptors to recover some of the encrypted files, but it's recommended to seek help from a professional or IT specialist for this method.
Don't be anxious about ransomware preventing you from accessing your files, as there are alternative solutions available that are easy to operate, which are detailed in the articles below.
Other Ransom Software
There are several types of ransomware that have been popular in recent years. One example is WannaCry, which was a global ransomware attack in 2017 that affected over 200,000 computers in over 150 countries.
- Locky:In 2016, Locky Ransomware encrypted over 160 file types through fake emails and attachments, specifically targeting files used by designers, developers, and engineers through phishing attacks.
- Wannacry: The Ransomware used an exploit called EternalBlue, which was originally developed by NASA. The hackers stole the exploit and used it to spread the Ransomware from computer to computer.
- BadRabbit: In 2017, a ransomware attack spread across media companies in Eastern Europe and Asia, causing significant disruption and financial losses.
- CryptoLocker: Launched in 2013, this Ransomware infected almost 500,000 machines.
- SimpleLocker: This was the first Ransomware to specifically target mobile devices, spreading through a Trojan downloader disguised as a legitimate app.
Conclusion
The Internet poses various threats, including viruses and other types of malware, which can often occur without our knowledge. To stay safe, it's essential to educate yourself about these cyber crimes and take necessary precautions, such as installing anti-malware software and backing up crucial data and files. By taking proactive steps, you can be one step ahead and minimize the impact of potential attacks.
FAQ About Ransomware
Below are some answers to the questions related to ransomware:
1. What causes a ransomware attack?
Ransomware attacks can occur without your involvement, often using phishing or malvertising tactics. To prevent this, exercise caution when opening emails and clicking on online ads, ensuring they are legitimate. Protect your system by securing and backing up all data and files, making it easier to recover in case of an attack.
2. Are ransomware threats real?
Ransomware threats are on the rise, driven by the lucrative benefits for cyber attackers. These malicious programs demand a ransom with a deadline, threatening to publish or block sensitive data if payment isn't made. This is a very real and alarming threat that requires attention and action to prevent.
3. What happens if you pay for ransomware?
The FBI advises against paying the ransom, as there's no guarantee of recovering the encrypted files. If you've already paid, contact your bank and local authorities. If you used a credit card, your bank may be able to block the transaction and return the funds. You can also report the scam to government fraud and scam reporting websites.
4. Does resetting a PC remove ransomware?
Resetting your PC will help remove the malware infection from your system. After the reset, install antivirus software and perform a full system scan to ensure your system is free of any additional risks.
Related Articles
- Automatically Copy Files When USB Drive Connected
- Solved: Taskbar/Start Button Not Working Windows 10
- Fixed: ATA/SATA Hard Drive Not Detected or Recognized in BIOS
- Hard Drive Not Spinning? Causes and Fixes Here!